Melbourne companies face more cyber-attacks than ever. One rogue email or an unpatched laptop can freeze projects, lose data and damage hard-won trust. Procision keeps you safe with local experts, proven tools and straight-forward advice. Your staff stay productive, your reputation stays intact and your monthly costs never spike without warning.
Small and mid-size firms do not need bank-grade systems. They need security that blends into today’s workflows and tomorrow’s growth.
What you get
Data Protection and Backup
Real-time visibility plus human expertise keeps threats from turning into incidents.
Data is your most valuable asset and the top target for ransomware gangs.
Key layers
Real-world result
In the past year our backup clients reported zero data-loss events despite stolen laptops, staff mistakes and power failures. One law firm even recovered an entire matter folder after it was deleted by accident the night before court.
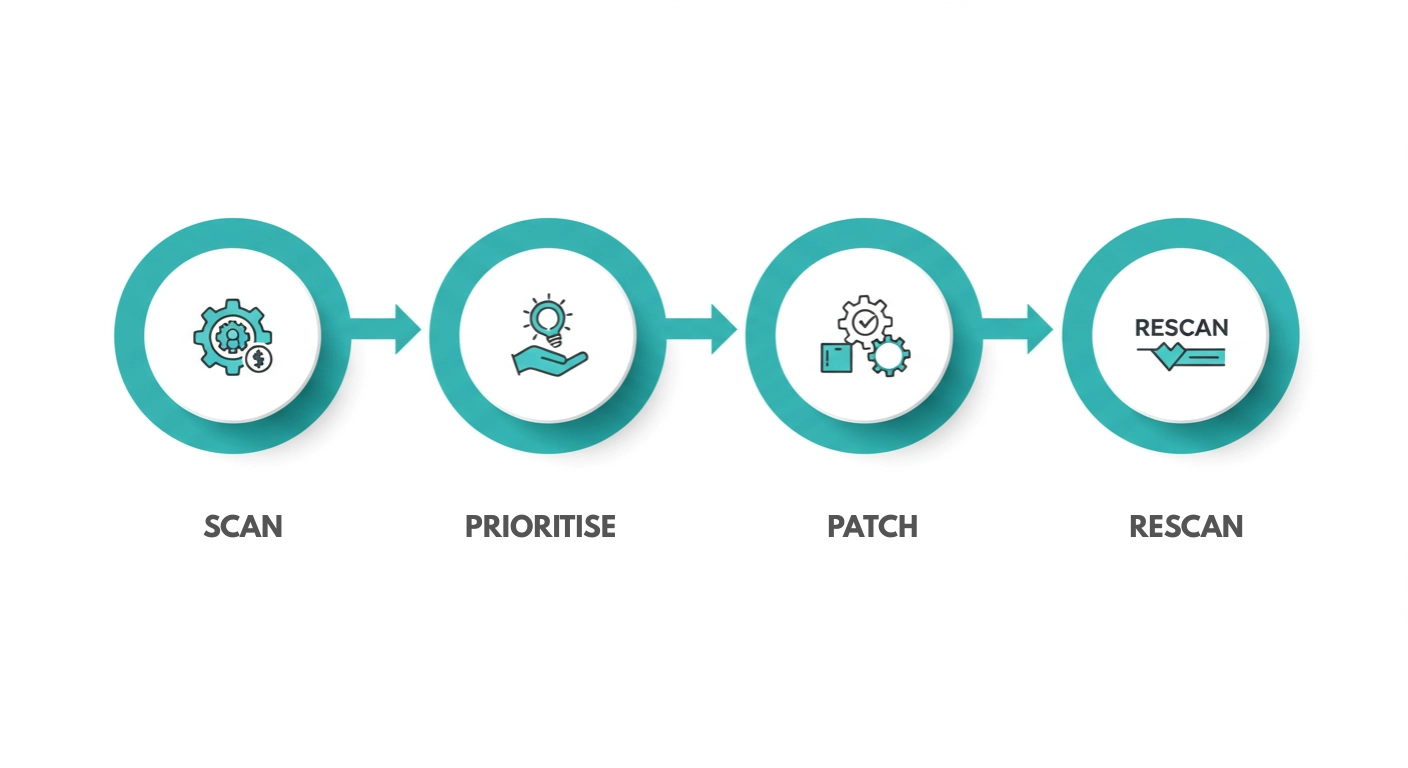
More than half of reported breaches start with an unpatched or misconfigured system. Procision closes that gap through a simple monthly cycle.
Critical patches are usually applied in under forty-eight hours, well ahead of most cyber-insurance requirements.
Compliance should clear a path, not block one. Our two-week sprint turns confusion into clarity.
What we do
Value to you
Attackers aim at inboxes and laptops because people are easy to trick. We close both doors before the knock.
Layers in place
Across our client base phishing clicks fall by more than fifty per cent within three months of rollout. That saves hours of password resets and keeps brand reputation intact.
Technology fails if people still click a fake invoice. We turn staff into your first line of defence.
How the programme works
Most firms cut repeat clickers to single digits in a single quarter, hitting common insurance clauses for “ongoing security awareness”.
A property management company specializing in parking facilities accidentally deleted a folder containing important tenant records and lease agreements during routine file maintenance. Thanks to Procision’s secure, automated backup solution—an integral part of our cyber security program—all documents were restored the same day. This rapid recovery ensured the company remained compliant with data retention policies and experienced no disruption to daily operations.
Result:
All tenant records and lease agreements fully recovered
No compliance or regulatory issues
Business operations continued without interruption
Increased staff confidence in IT support and data security
| Package | Main Deliverables | Ideal Size | From Price |
|---|---|---|---|
| Essential Protect | Monitoring and patching every day | 15-150 users | AUD 39 per user / month |
| Secure Backup & DR | Immutable off-site backup plus test restores | Any size | AUD 95 per server / month |
| Compliance Starter | Essential Eight gap review and policy pack | Regulated SMEs | AUD 2,400 one-off |
| Phishing Defence | AI spam filter plus monthly phishing drills | 25-250 mailboxes | AUD 4 per mailbox / month |
Procision has secured Melbourne organisations since 2003 and now protects more than fifty firms across finance, legal, design and professional services.
Proof points
Content reviewed by the Senior Network Security Consulting Team at Procision.
Any organisation that stores customer or financial data, relies on email or cloud apps, or must meet compliance rules—essentially every small-to-medium Melbourne business today.
A managed program that monitors, defends and responds to threats across your network, endpoints, cloud and email, typically bundling 24/7 monitoring, patching, backup and incident response.
Most Australian SMBs spend A $35–A $60 per user per month for a full managed security package; specialised extras (e.g., penetration tests) are quoted separately.
1) Network security, 2) Endpoint security, 3) Cloud security, 4) Application security and 5) Data security—all of which Procision can deliver as integrated managed services or targeted projects.
Getting started is easy—just book a quick call to discuss your needs. You’ll receive a free gap report showing how your security measures compare to best practices. If you’re happy with the plan and price, we’ll handle setup and training so you can go live within a week.
Procision is a leading Melbourne-based IT partner, providing expert managed services and strategic consulting to businesses across Australia. We are committed to delivering professional, precise, and value-driven IT solutions.



Stay ahead of the tech curve! Get the latest IT insights and solutions delivered to your inbox.
By subscribing, you agree to our Privacy Policy & Terms and Conditions